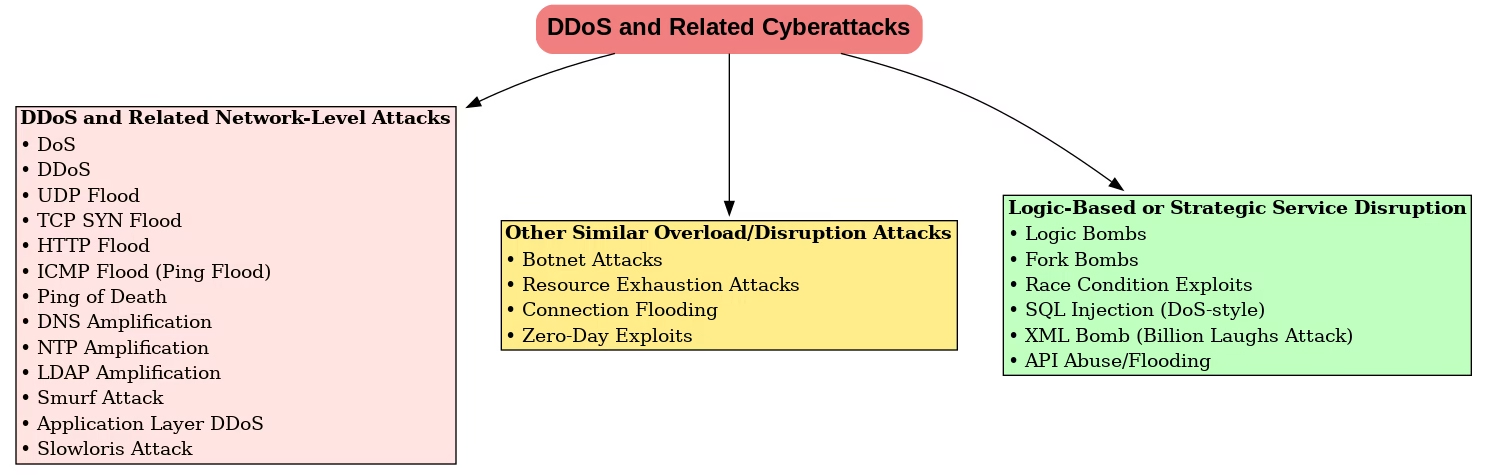
Understanding Common Cyberattacks: From DoS to Application-Level Threats part-2
Part 2 – Resource Exhaustion & Logic-Based Attacks 📘 Disclaimer: This article is intended solely for cybersecurity awareness and educational purposes. It does not endorse or promote any form of unauthorized access, attack simulation, or malicious activity. 📘 This is the second part of a two-part series. In Part 1, we explored foundational network-layer attacks … Read more