Introduction to Active Directory Security
When setting up Active Directory (AD), security must be a top priority. Every level of the system, from small details to large configurations, needs attention. This includes managing AD users, security groups, organizational units (OUs), group policies, user access rights, patching, firewalls, network security, and encryption protocols.
In my experience, many environments with over 100 users have poorly structured AD setups. For example, placing all users in the default “Users” OU is a common mistake. This practice results in users—whether CEOs, HR, IT, or Finance—being grouped together and inheriting the same permissions, which creates significant security risks.
The same issue applies to computer accounts. Without a proper OU structure, it becomes difficult to manage group policies, apply security settings, and assign administrative rights effectively. To prevent these risks, a well-planned AD structure is essential for both security and management.
Best Practices to Secure Active Directory:
1. Principle of Least Privilege
- Limit user and group privileges to only what’s necessary.
- Avoid broad administrative rights; use role-based access control (RBAC).
- Harden permissions with Group Policy.
2. Implement Strong Authentication Mechanisms
- Enable Multi-Factor Authentication (MFA) for privileged accounts and critical systems.
- Enforce strong passwords, implement password expiration, and consider biometrics or hardware tokens for authentication.
3. Secure Administrative Accounts
- Use dedicated admin accounts separate from regular user accounts.
- Audit memberships in admin groups like Domain Admins and Enterprise Admins.
- Apply administrative tiering (e.g., Tier 0 for Domain Admins, Tier 1 for server admins).
4. Regularly Review and Audit Active Directory
- Perform regular audits of user/group permissions with auditing tools.
- Monitor logins and failed login attempts for suspicious activity.
- Configure Group Policy Objects (GPOs) for audit policies and link them to appropriate OUs.
- Review security logs for event IDs like 4624 (successful login) and 4625 (failed login attempt). Navigate to Event Viewer > Windows Logs > Security.
5. Implement Group Policy Security Settings
- Configure password, lockout, and audit policies through GPOs.
- Restrict anonymous access by disabling anonymous enumeration of SAM accounts.
A) Some policies can be configured as follows:
- Password Policy:
Location: Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy - Account Lockout Policy:
Location: Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Account Lockout Policy - Audit Policies:
Location: Computer Configuration > Policies > Windows Settings > Security Settings > Advanced Audit Policy Configuration > Audit Policies
Enable auditing for events like logons/logoffs, account logons, and object access.
6. Limit Access to Sensitive AD Objects
- Use Access Control Lists (ACLs) to restrict permissions on sensitive AD objects.
- Set proper delegation of control for AD management.
- Configure Fine-Grained Password Policies for better granularity.
7. Secure AD Replication
- Limit replication traffic by using IPsec or encryption.
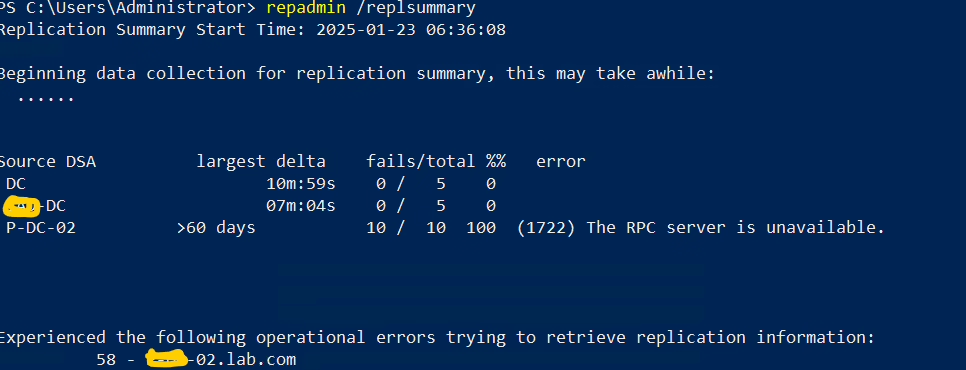
- Regularly monitor AD replication health using repadmin commands, ensuring replication is occurring without errors.
- Use command repadmin /replsummary
See above result one of my DC is not available from long time. We have to troubleshoot accordingly to find out the issue. In my case server is powered off.
- Command to check Replication Status of Specific Domain Controllers:
repadmin /showrepl <DC_Name>
8. Regular Backups and Recovery Planning
- Perform regular backups of AD, including system state backups.
- Test your AD disaster recovery plan to ensure swift restoration in case of an incident.
9. Protect Against Pass-the-Hash and Other Attacks
- Use Kerberos authentication over NTLM to mitigate pass-the-hash attacks.
- Disable SMBv1 to protect against attacks like WannaCry.
- Use Windows Defender Credential Guard to protect credentials.
10. Review and Implement Proper OU Structure
The goal is to design your OU structure thoughtfully to simplify resource management, enhance security, and ensure proper delegation of administrative tasks. Avoid overly complex or overly broad OU setups that could complicate management for critical systems.
- Use a well-organized OU structure to delegate permissions and isolate resources more effectively.
- Avoid overly broad or deeply nested OUs for critical infrastructure resources.
11. Patch and Update AD Servers Regularly
- Keep domain controllers and AD-related servers up-to-date with security patches.
- Test patches in a non-production environment before applying them to production systems.
12. Monitor Privilege Escalation
- Review security logs for signs of privilege escalation.
- Implement time-based privileges for administrative tasks to minimize risks.
Monthly Audit:
Regularly audit critical groups like Domain Admins, Enterprise Admins, and Schema Admins to ensure only authorized users are members. You can use PowerShell commands like:
Get-ADGroupMember ‘domain admins’ | ft name, samaccountname > c:\temp\DomainAdmins.txt
Get-ADGroupMember ‘schema admins’ | ft name, samaccountname > c:\temp\SchemaAdmins.txt
Get-ADGroupMember ‘enterpriseadmins’ | ft name, samaccountname >c:\temp\EnterpriseAdmins.txt
Conclusion
By following these best practices, you reduce the likelihood of security breaches, improve your AD environment’s resilience, and protect sensitive information. Regular audits, strong authentication, and a well-thought-out OU design are essential to maintaining a secure and manageable AD infrastructure.
Note: This article is based on my expertise and experience. However, it’s not necessary to implement everything mentioned here. It’s important to review these suggestions, understand them, and make decisions based on your unique environment. Every environment may require its own approach, but most organizations typically follow these practices.
If you found these best practices useful, explore our other in-depth articles on Active Directory security and best practices. Subscribe to our newsletter for more expert advice delivered to your inbox!