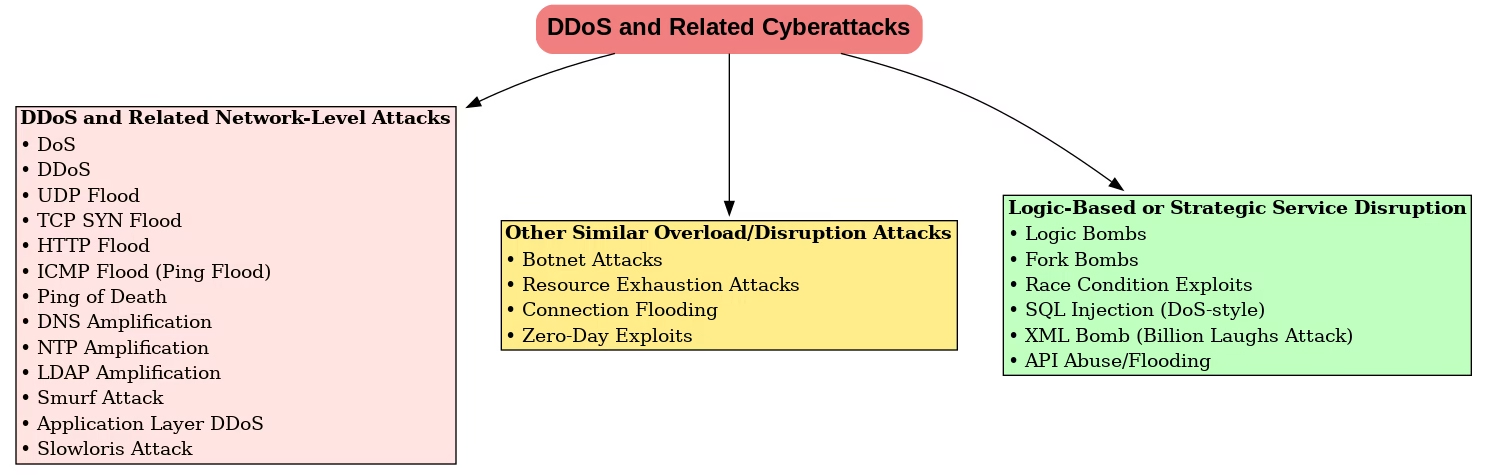
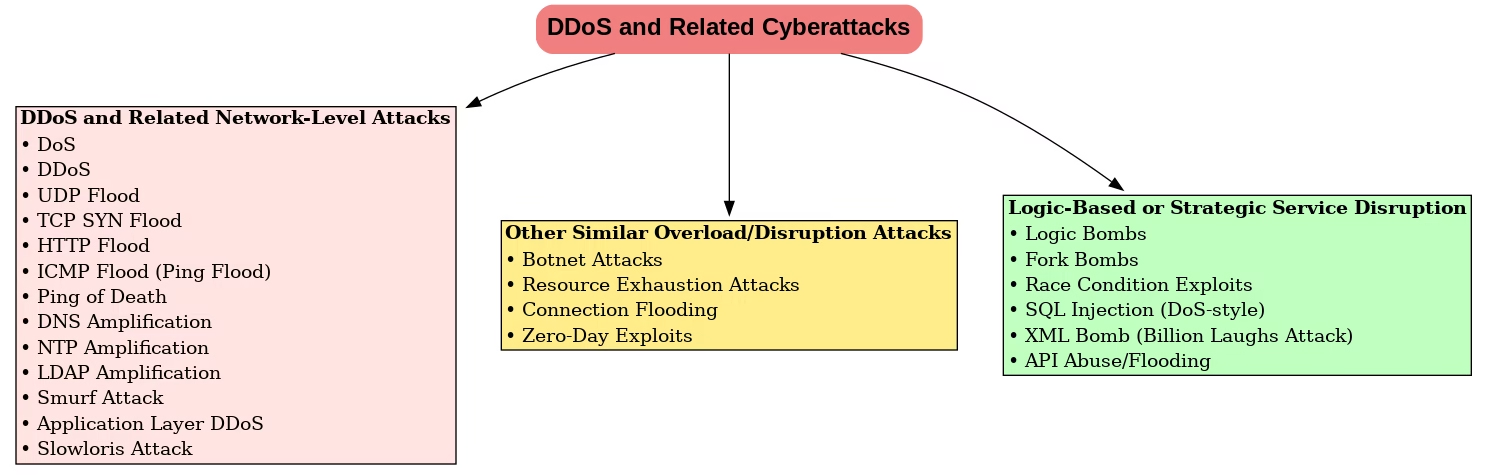
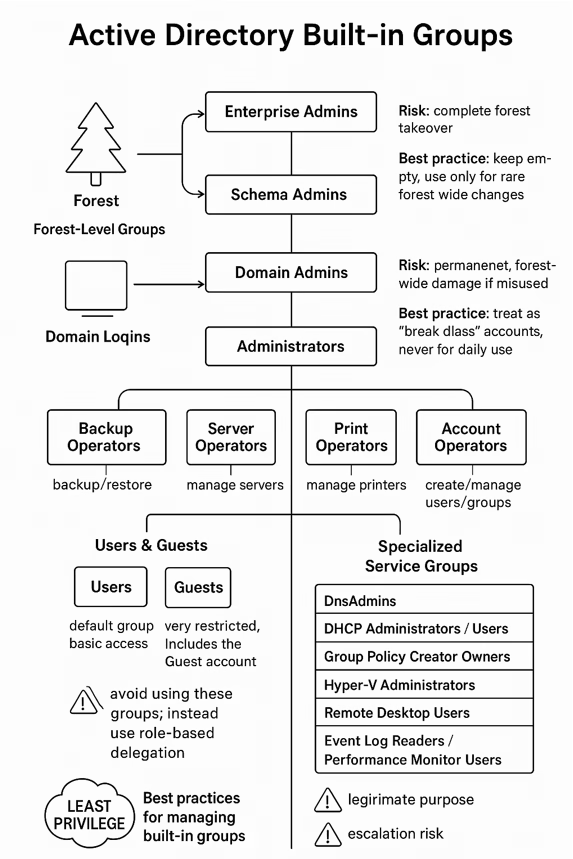
🔐 Microsoft 365 Defender: The Ultimate All-in-One Cybersecurity Solution
🌍 The New Era of Cyber Threats Let’s be real — the internet isn’t what it used to be. Cyber threats today are faster, smarter, and far more dangerous than the simple viruses of the past. Attackers now use AI-powered phishing, identity theft, and multi-stage ransomware campaigns that can cripple entire businesses in minutes. That’s … Read more