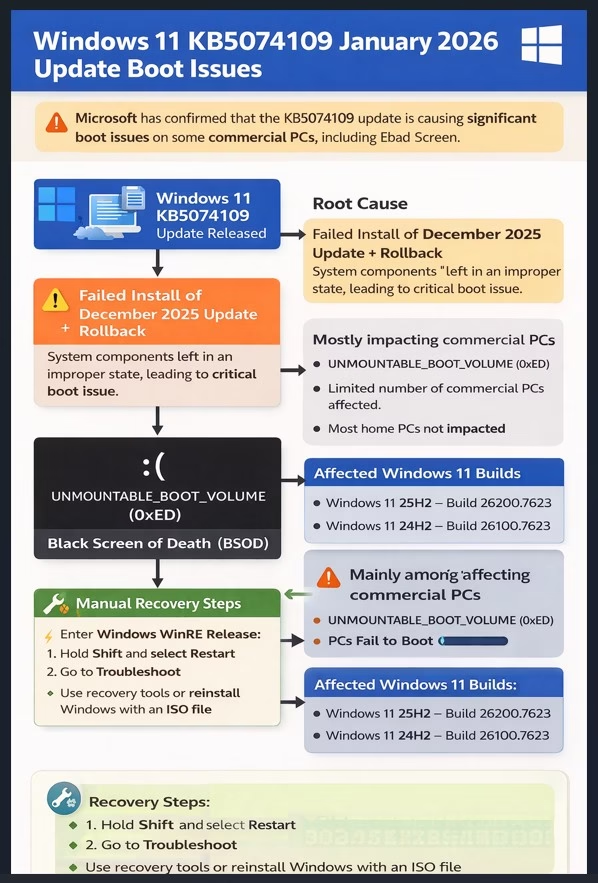
Microsoft Confirms Windows 11 KB5074109 January Update Causes BSOD and Boot Issues on Some Commercial PCs
Microsoft has confirmed that the Windows 11 KB5074109 January 2026 update is causing significant boot issues, including the Black Screen of Death (BSOD), on a limited number of commercial (non-consumer) PCs. This problem does not seem to impact the majority of home users, and Microsoft has already taken steps to ensure it does not affect … Read more