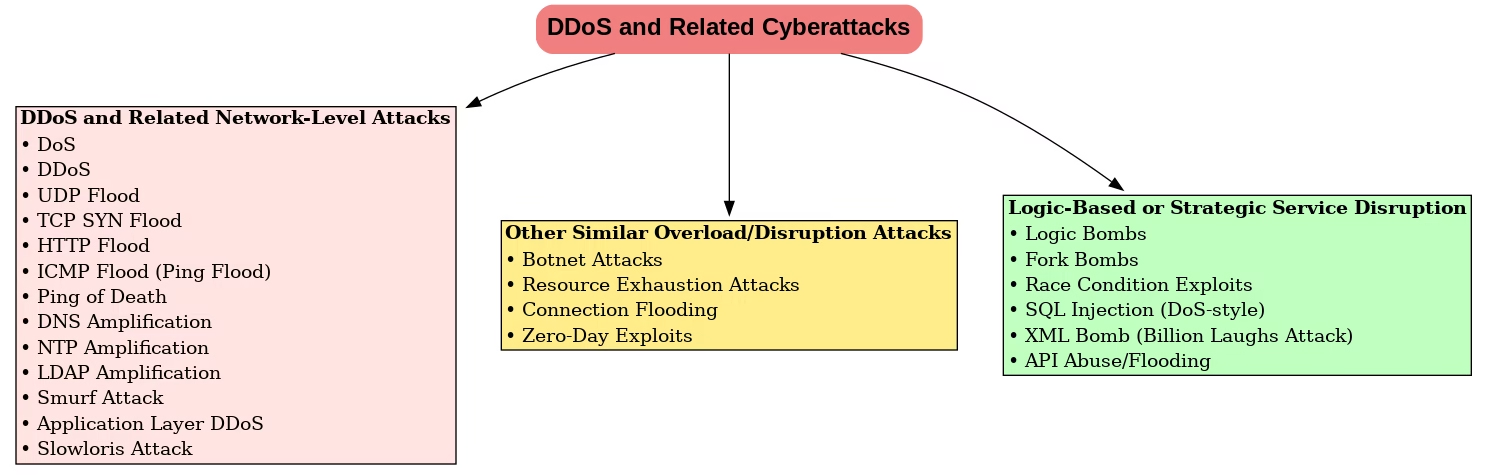
While reading about cybersecurity recently, I was inspired to write an article that brings together various types of cyberattacks in one place. In the IT world, we frequently encounter such threats whether directly or indirectly making it important to understand how they work. Although some of these attacks have known mitigations today, many legacy systems remain vulnerable, leaving organizations exposed.
In our increasingly connected world, cyberattacks continue to disrupt businesses, users, and services globally. This article aims to demystify some of the most common forms of Denial of Service (DoS), Distributed Denial of Service (DDoS), and related network attacks. Through clear concepts, real-world examples, everyday analogies, and defensive strategies, we’ll explore how these attacks operate and how to guard against them.
1. DoS (Denial of Service)
Concept
A single attacker floods a target with traffic or requests until resources are exhausted and the service becomes unavailable.
Real-World Example
In 2000, Mafiaboy used DoS techniques to knock sites like CNN and Yahoo offline.
Everyday Example
Like one person repeatedly calling your phone nonstop so no one else can get through.
Defense
- Rate limiting to cap requests per IP
- Firewalls to block bad sources
- IDS/IPS to detect abnormal spikes
- Load balancing to distribute traffic
2. DDoS (Distributed Denial of Service)
Concept
A coordinated attack using many compromised devices (botnet) to overwhelm a target with massive traffic.
Real-World Example
Mirai (2016) used IoT devices to flood Dyn DNS and disrupted Netflix, Twitter, and Reddit.
Everyday Example
Like thousands of people crowding a store entrance so real customers can’t enter.
Defense
- DDoS protection/scrubbing services (Cloudflare, AWS Shield, etc.)
- CDNs and global load balancing
- IP filtering & geo-blocking for suspicious regions
- Real-time traffic analysis to spot bot patterns
3. UDP Flood
Concept
Attackers send a huge volume of UDP packets (often to random ports), forcing servers to reply or be overwhelmed.
Real-World Example
Game services (e.g., Xbox Live) have been taken offline by UDP floods.
Everyday Example
Like someone knocking on every door in a building rapidly so no one can answer properly.
Defense
- Block unnecessary UDP ports at the edge
- Apply rate limiting for UDP traffic
- Use IDS/IPS to detect abnormal UDP volumes
4. TCP SYN Flood
Concept
Sends many SYN (connection) requests but never completes the handshake, filling the server’s connection table.
Real-World Example
SYN floods were used to target government services during conflicts, e.g., Georgia (2008).
Everyday Example
Like reserving every table at a restaurant with fake names so real guests have nowhere to sit.
Defense
- SYN cookies to validate connections
- Increase backlog queue (temporary relief)
- Drop incomplete handshakes with firewalls or proxies
5. HTTP Flood
Concept
High volumes of legitimate-looking HTTP requests (GET/POST) overload web applications and backend systems.
Real-World Example
GitHub faced enormous HTTP request floods (1.35 Tbps reported in attack vectors).
Everyday Example
Thousands of people browsing your store constantly without buying, blocking real customers.
Defense
- WAFs to identify and block malicious patterns
- CAPTCHA or challenge response for suspicious sessions
- Behavioral analysis to separate bots from humans
6. ICMP Flood (Ping Flood)
Concept
A flood of ICMP Echo (ping) requests overwhelms the target’s network or CPU.
Real-World Example
Earlier internet eras saw many servers disrupted by heavy ping floods.
Everyday Example
Someone repeatedly shouting “Are you there?” so often you can’t focus on anything else.
Defense
- Limit ICMP at the firewall or router
- Implement anti-spoofing filters
- Monitor and alert on unusually high ICMP rates
7. Ping of Death
Concept
Sends oversized or malformed ICMP packets that can crash or freeze vulnerable systems.
Real-World Example
Legacy routers and older OS versions would sometimes crash on oversized pings.
Everyday Example
Sending a letter so big and malformed that the mailbox breaks trying to accept it.
Defense
- Patch and update old/legacy devices
- Drop malformed packets at the network edge
- Use modern OS/network stacks that validate packet sizes
8. DNS Amplification
Concept
Attacker sends small spoofed DNS queries to open resolvers; resolvers reply with much larger responses sent to the victim, amplifying traffic.
Real-World Example
The 2013 Spamhaus attack reached >300 Gbps using DNS amplification.
Everyday Example
Asking a library for a quick note and having them mail an encyclopedia to someone else over and over.
Defense
- Disable open DNS resolvers or restrict them to trusted clients
- Enable response rate limiting (RRL) on DNS servers
- Implement DNSSEC and proper access controls
9. NTP Amplification
Concept
Exploits older NTP servers (e.g., the monlist command) to turn a small request into a large reply to a spoofed victim.
Real-World Example
Large NTP amplification attacks (2014) produced traffic >400 Gbps.
Everyday Example
Asking for “today’s visitor list” and getting a huge binder of everyone who ever visited.
Defense
- Disable monlist or upgrade NTP software
- Block or rate-limit NTP responses to untrusted sources
- Apply anti-spoofing on network edges
10. LDAP Amplification
Concept
Uses misconfigured or open LDAP servers to reflect and amplify responses to a victim when queries are spoofed.
Real-World Example
Attackers have used LDAP reflection to overwhelm small services with amplified replies.
Everyday Example
Whispering into a loudspeaker while pretending to be someone else — the speaker blasts the message out.
Defense
- Restrict LDAP to internal/trusted networks only
- Disable anonymous binds and public search access
- Monitor query/response ratios for abnormal amplification
11. Smurf Attack
Concept
Attacker sends spoofed ICMP requests to a network’s broadcast address, causing all hosts on that network to reply to the victim.
Real-World Example
Common in the 1990s; mitigated today by proper router defaults and ingress filtering.
Everyday Example
Sending an invitation to every house in town with your neighbor’s address — now everyone shows up at their door.
Defense
- Disable IP-directed broadcasts on routers
- Implement ingress/egress filtering to block spoofed sources
- Restrict ICMP handling on internal networks
12. Application-Layer DDoS (Layer 7 Attacks)
Concept
Targets specific application features (login pages, search, checkout) with intelligent, low-rate traffic that mimics real users. These attacks are stealthier because they look “normal.”
Real-World Example
Attackers target login endpoints during credential-stuffing or shopping cart during flash sales to cause maximum disruption.
Everyday Example
Lots of fake customers using your checkout flow repeatedly so genuine buyers can’t complete purchases.
Defense
- Rate-limit sensitive endpoints (per IP/user/API key)
- Apply progressive challenges (CAPTCHA, progressive profiling)
- Use RUM, tracing, and WAF rules to spot anomalies in user behavior
13. Slowloris Attack
Concept
Keeps many connections open by sending partial HTTP headers slowly. The server keeps waiting for completion and exhausts connection slots.
Real-World Example
Slowloris caused widespread outages for Apache-based sites around 2009.
Everyday Example
Someone speaking so slowly on a call that the line is occupied indefinitely.
Defense
- Enforce request timeouts and minimum progress thresholds
- Use reverse proxies/load balancers that handle slow clients efficiently
- Monitor for large numbers of partial/incomplete requests
Conclusion (Part 1)
Network-level attacks vary from straightforward traffic floods to sophisticated reflection and amplification methods. Key defenses involve regular patching to keep the system up to date with vulnerability patches and related updates, stringent access controls, rate limiting, deployment of WAFs (Web Application Firewalls), CDNs (Content Delivery Networks), and specialized DDoS mitigation services. For larger or more complex attacks, a layered approach combining prevention, real-time detection, and third-party mitigation is essential.
Coming Up Next: Part 2 will explore other overload and disruption techniques, including botnets, resource exhaustion, race conditions, XML/SQL bombs, API abuse, and more.