Introduction
Most AD administrators are already familiar with the pros and cons of the built-in Administrator account in Active Directory. I’m simply trying to explore and understand it more clearly using diagrams and articles.
Active Directory (AD) is the backbone of identity and access management in most enterprises. To simplify administration, Microsoft provides a number of built-in groups with predefined privileges. These groups make it easier to assign permissions, but they also carry serious security risks if misused.
In this article, I explain the major built-in groups, explain what they do, highlight potential risks, and provide best practices for managing them securely.
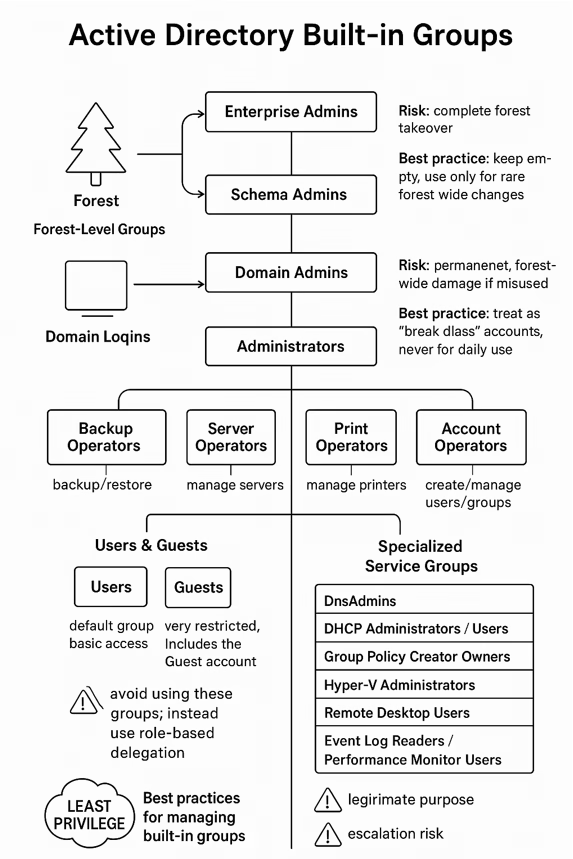
Forest-Level Groups
Enterprise Admins (EA)
- Scope: Entire forest.
- Rights: Add/remove domains, create forest trusts, raise forest functional levels.
- Risk: A compromised account can take over the entire forest.
- Best Practice: Keep this group empty unless performing forest-wide changes.
Schema Admins (SA)
- Scope: Forest schema (the blueprint of AD objects).
- Rights: Modify schema attributes and classes.
- Risk: Permanent, forest-wide damage if schema is altered incorrectly.
- Best Practice: Use only during schema extensions (e.g., Azure AD connect feature, installing Exchange) and remove membership immediately afterward.
Domain-Level Groups
Domain Admins (DA)
- Scope: Single domain.
- Rights: Full control of domain resources; automatically an admin on all domain-joined machines.
- Risk: If compromised, attacker owns the entire domain.
- Best Practice: Treat as “break glass” accounts — never for daily use.
Administrators (BA)
- Scope: Domain controllers & AD objects.
- Rights: Unrestricted access, including ownership of objects.
- Risk: Too much power concentrated in one group.
- Best Practice: Keep membership to the bare minimum, monitor closely.
Operator Groups
These groups were designed to delegate specific tasks but often grant more access than expected:
- Backup Operators → Override permissions to backup/restore files.
- Server Operators → Manage servers (shutdown, backup, time changes).
- Print Operators → Manage printers and install drivers.
- Account Operators → Create and manage users/groups (except admins).
Risk: For example, Print Operators can install drivers with SYSTEM-level rights — a common privilege escalation path.
Best Practice: Avoid using these groups; instead, use role-based delegation.
User and Guest Groups
- Users → Default group for all accounts; basic rights like logging in and reading directory info.
- Guests → Very restricted; includes the Guest account (disabled by default).
Risk: Guest accounts are often abused for unauthorized access.
Best Practice: Keep Guest disabled unless absolutely necessary.
Specialized Service Groups
Active Directory also includes service-specific groups:
- DnsAdmins → Manage DNS servers (known escalation path).
- DHCP Administrators/Users → Manage DHCP roles.
- Group Policy Creator Owners → Create and edit GPOs.
- Hyper-V Administrators → Manage virtualization.
- Remote Desktop Users → Allow RDP login.
- Event Log Readers / Performance Monitor Users → Access logs and performance data.
Risk: Even service groups can be misused. For example, DnsAdmins can be leveraged for domain compromise.
Best Practice: Assign only when required, and review memberships regularly.
Best Practices for Managing Built-in Groups
- Principle of Least Privilege – Users should only have the permissions necessary for their role.
- Privileged Identity Management (PIM) – Use just-in-time access for high-privilege roles.
- Separate Admin & User Accounts – Admins should have a normal user account and a separate admin account.
- Audit Memberships Regularly – Especially for Enterprise Admins, Domain Admins, and Schema Admins.
- Monitor Activity – Use SIEM or Azure AD monitoring to track privileged group changes.
Conclusion
Active Directory built-in groups are powerful tools that simplify administration, but they can also open the door to complete domain or forest compromise if poorly managed. By understanding what each group does, restricting membership, and following best practices, organizations can secure their AD environment and reduce risk.
Think of them like master keys — you absolutely need them, but you don’t hand them out freely. Keep them locked down, only use them when necessary, and always know exactly who has them.