Introduction
A friend of mine who works in IT recently reached out with a question about password policies in Active Directory (AD). He wanted to set up a password policy for a specific group of users, but he was having trouble making it work. After some investigation, I realized he missed an important detail about how Active Directory password policies function. This article will walk you through the process of configuring password policies, especially Fine-Grained Password Policies (FGPP), for specific users or groups.
Understanding Password Policies in Active Directory
Active Directory (AD) allows administrators to enforce password policies to enhance security. These policies include requirements for password complexity, minimum length, expiration, and history. Password policies can be applied in two primary ways:
- All Domain Users: A single policy applies to everyone in the domain.
- Specific Groups of Users: A policy is applied to specific users or security groups.
Default Domain Policy
- What It Does: Password policies for domain accounts are generally enforced by the Default Domain Policy or another Group Policy Object (GPO) linked at the domain root.
- How It Works: If you modify the password settings in the Default Domain Policy, the changes will automatically apply to all users in the domain.
Fine-Grained Password Policies (FGPP)
If you need to apply different password policies for specific users or groups, Fine-Grained Password Policies (FGPP) come into play. Here’s what you need to know:
- What They Are: FGPPs allow you to configure password policies that override the Default Domain Policy for certain users or security groups.
- Where They’re Configured: These policies are created in the Password Settings Container within Active Directory and apply only to specific users or groups.
Why GPOs Linked to OUs Don’t Work for Domain Password Policies.
One common mistake when implementing password policies is linking a Group Policy Object (GPO) to an Organizational Unit (OU). However, GPOs linked to OUs do not apply to domain users. Here’s why:
- Domain-level Enforcement: Domain controllers enforce password policies only at the domain level or through FGPP.
- Local Accounts Only: GPOs linked to OUs can only enforce password policies for local accounts on computers within that OU—not for domain users.
How to Implement Password Policies in Active Directory
Let’s walk through two options for applying password policies in Active Directory.
Option 1: Modify the Default Domain Policy
If you want to apply a single password policy for all domain users, you can modify the Default Domain Policy:
- Open the Group Policy Management Console (GPMC).
- Edit the Default Domain Policy.
- Navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policies > Password Policy.
- Configure your desired password settings (e.g., complexity requirements, minimum length, password history).
- Save the policy and allow time for replication across domain controllers.
Option 2: Create a Fine-Grained Password Policy (FGPP)
To apply different password policies to specific users or groups, follow these steps:
- Open the Active Directory Administrative Center (ADAC).
- Navigate to System > Password Settings Container.
- Right-click and select New > Password Settings.
- Configure the following settings:
- Name: Provide a descriptive name (e.g., “HR Password Policy”).
- Precedence: Set priority (lower numbers have higher priority).
- Password Settings: Configure password complexity, minimum length, history, etc.
- Under Directly Applies To, add the specific users or security groups the policy will apply to.
- Save the policy.
Verifying Fine-Grained Password Policy (FGPP) Application
You can verify the applied password policy for a user using PowerShell with the following command:
Get-ADUserResultantPasswordPolicy -Identity <username>
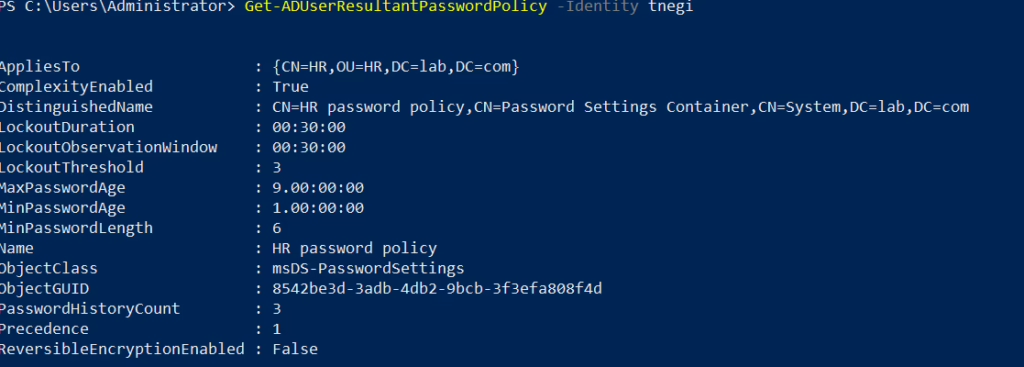
This command will show you the Fine-Grained Password Policy that has been applied to a specific user.
Example: Using gpresult to Check Group Policies
To see the group policies applied to a user or computer, use the gpresult command. Since password policies for domain accounts are enforced at the domain level, the Default Domain Policy settings will be reflected in the gpresult output. Here’s an example command:
gpresult /USER tnegi /h C:\gpresult_user8.html
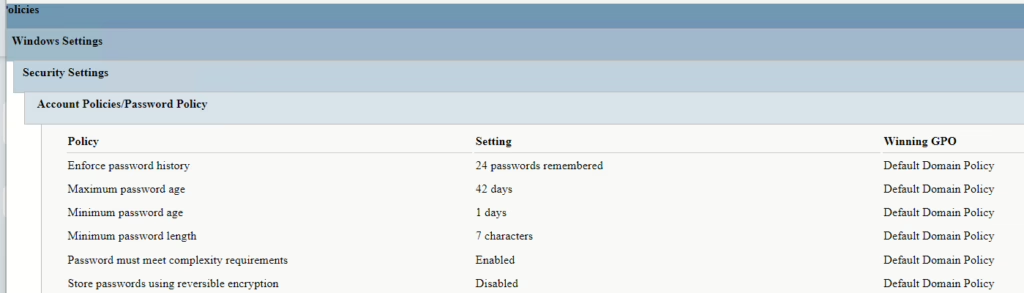
If no FGPP is applied, the Default Domain Policy settings will be the effective password policy.
Key Takeaways
- Default Domain Policy: Applies to all domain users and is configured at the domain level.
- Fine-Grained Password Policies (FGPP): Allow for different password policies for specific users or security groups.
- OU-Linked GPOs: Do not affect domain user password policies—only local accounts on the computers within that OU.
Why Share This Knowledge?
Implementing password policies in Active Directory can be confusing, especially for beginners. Misunderstanding how these policies work can lead to wasted time and troubleshooting frustrations. By understanding the difference between Default Domain Policy and Fine-Grained Password Policies, you’ll be able to apply the correct policies and avoid common mistakes.
For those managing Active Directory, having a solid grasp of these principles will save you time and effort. I hope this article has helped clarify the process of configuring password policies. Feel free to share your thoughts or ask any questions in the comments below—I’d love to hear your experiences!